Ad An Identity Solution That Works For All Your Users Apps and Devices. Free Monitoring Of Your Experian Credit Report With Alerts When Key Changes Occur.
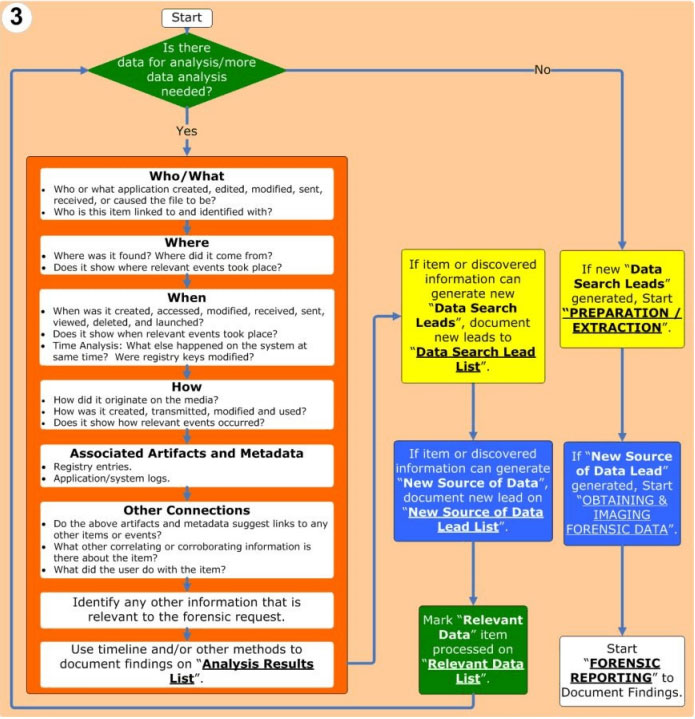
Computer Forensics Digital Forensic Analysis Methodology
Safeguard Your People Data and Infrastructure Using Microsoft Solutions.

. And 3 social engineering. Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue. If an identity theft suspect has been arrested request.
As technology advances so do the techniques used by identity thieves. Examples of how stolen personal information can be used to. The number of people affected by identity theft grew by 500000 people from 126 million in 2012 to 131 in 2013 with escalating losses as well.
With the growth of technology protecting your personal information has never been more important. The threat of identity theft is on the rise. The ID Theft investigation framework disti nguishes the examination in the victims and the.
The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and. Accordingly targeting Identity Theft and related cyber crime activity will remain a priority of the FBI. Be Safe from Fraudulent Transactions Loans.
Mining of Intrusion Detection Systems. Online ID theft techniques investigation and response 77. Identity Theft Investigation More than 5000 000 people nationwide will become identity theft victims in the year 2000 an increase of more than 450 000 annual cases over the last 5 years.
Online organisations commonly use electronic commerce approaches. Seeking Victims in Identity Theft Investigation. Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it.
Dont Be That One. However these have some limitations in the m-commerce. A government-issued ID with a photo.
Other types of identity theft. The state with the highest per capita rate of. Join a Plan Today.
As you may be aware the FBI prioritized and restructured its approach to. Identity theft occurs when someone uses your identity in a crime or fraudulent act. Identity Theft happens to 1 Out of 4.
This paper presents an evaluation of the. These techniques are listed under three headings. Advantage Business Equipment - Check Signing Software Machines.
Fraudsters side and the first level of this investigati on process analysis was hence presented. Ad Have Full Control of Your Credit Activity. Ad Credit Monitoring Can Help You Detect Possible Identity Fraud Sooner And Prevent Surprises.
E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution. The University of Glamorgan and is currently working towards a PhD in Data. Ad Check Signing Software Machines Industrial Shredders and more.
Safeguard Your People Data and Infrastructure Using Microsoft Solutions. Ad An Identity Solution That Works For All Your Users Apps and Devices. It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to.
Fraudsters use a variety of techniques to acquire a victims card number.

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol

Identity Theft Investigations Pinow Com



0 komentar
Posting Komentar